IT Certifications
IT Jobs - What's Out There? -

In this article, we would like to point out the obvious
IT Jobs that at times get overlooked. Find out what's out there and which
information technology is the right choice for you. From people that create
laptop computers to folks that do
web design to
developers that come up with
computer software concepts from scratch. Also a bit at the end about
computer schools and
computer training.

How to Assign Static IP Address in Windows Server 2008 R2 -
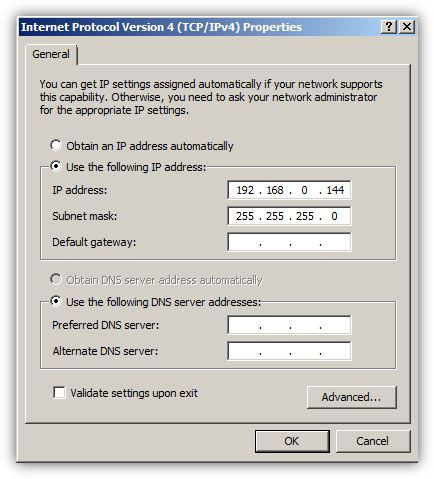
An IP address is a 32-bit number divided in 4 octal numbers and each octal separated by a '.' (dot), technically knows as a period. Administrators assign IP addresses to the computers so that they can be uniquely identified in a local area network and can communicate and exchange information with other computers in the network. IP addresses can be assigned to the computers either manually (static IP addresses) or through DHCP servers (dynamic IP addresses). When administrators plan to assign dynamic IP addresses to the computers they must configure DHCP servers with appropriate IP addressing schemes do accomplish the task. On the other hand, if administrators plan to assign static IP addresses to the computers they must manually go to each computer system in ...

Leaping Ahead in WiFi Standard - 802.11ac -

We all know that we need more bandwidth now, than we ever did in the past. There tons more online games, online movies, online collab work, you name it. And the past standards of Wifi namely 802.11a, 802.11b, 802.11g, 802.11n, and so on) were getting better and better; however, the 802.11ac does the trick. Well, atleast for now it is, until something better comes along.
Understanding DNS Servers -

Domain Name System or DNS servers are dedicated computers that have network operating systems installed on them and are responsible for resolving hostnames (computer names) to their IP addresses and vice versa. DNS servers are used worldwide and are helpful while accessing the Internet and visiting websites. Every Internet Service Provider or ISP has its own DNS server which receives name resolution requests from the subscribers of that ISP and resolves the requested host names to their corresponding IP addresses.

Understanding Mesh Topology -

Apart from star topology that is widely used in almost every network environment, the other type of topology that is complex while setting up but provides 100% fault tolerance to the network is Mesh Topology. In this topology, every computer that has to be connected to the network is connected to every computer that is available in the network. For example if there are four computers namely A, B, C and D, then A will be connected to B, C and D. Likewise B will be connected to A, C and D and so on. This means that when mesh topology is used while establishing a network setup, it is very unlikely that the network would ever face congestions or would ever fail.

How to Share a Folder in Windows Server 2008 R2 -
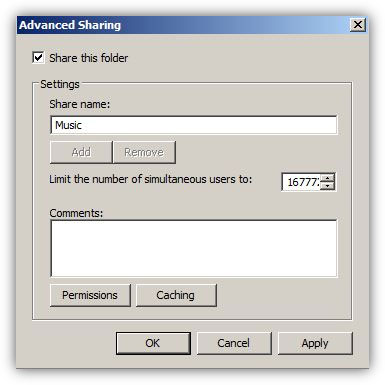
In organizations or home setups where there are multiple computers connected to each other, in order to transfer files from one computer to another administrators use to share the folders on one computer (generally known as file server) and make them accessible from all other computers in the network. In order to do so administrators normally configure and set NTFS and share permissions on the shared folders which, as a result, help them control the accessibility of user accounts or groups on them.
Types of Servers 2 -

One of most important type of server is cluster servers. Software that enables clustering of servers is installed into a computer. Clustering servers also serve as load balancing servers between two computers. This is a common small business server. Clustering servers are used to avoid server failover. Server failover is the capability to shift to another standby server if the main server fails.

How to Change Windows Server 2008 R2 Computer Name -
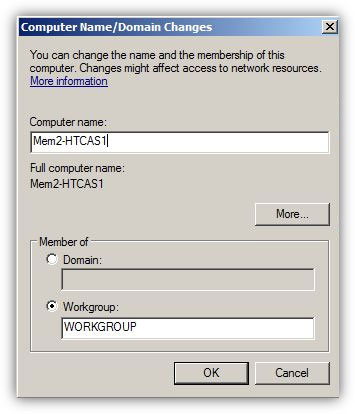
In any computer that runs any operating system of any platform, computer name plays an important role when it comes to its identification. Name that an administrator assigns to a computer must be unique for that computer in the entire network. In case, because of errors or deliberately, administrators assign identical names to 2 or more computers, all the computers with common names stop communicating with other computers in the network. In Microsoft Windows platform computer names are also known as hostnames. When administrators install Microsoft Windows operating systems on the computers, operating systems automatically generate random ...

Computer Certification Training in Houston -
![Zend Certification]()
I live in Magnolia, TX area which is just North West of Houston. I'm sure, all that I would need is to maybe get a couple of community college classes to brush up on the fundamentals of programming, then maybe a few hours training on PHP to get up to speed. Finally, I'll need a few hours training for the Zend Certification itself, right? I mean this is the United States of America. We invented most of this stuff.
Installing DHCP Server Role on Windows Server 2008 R2 -
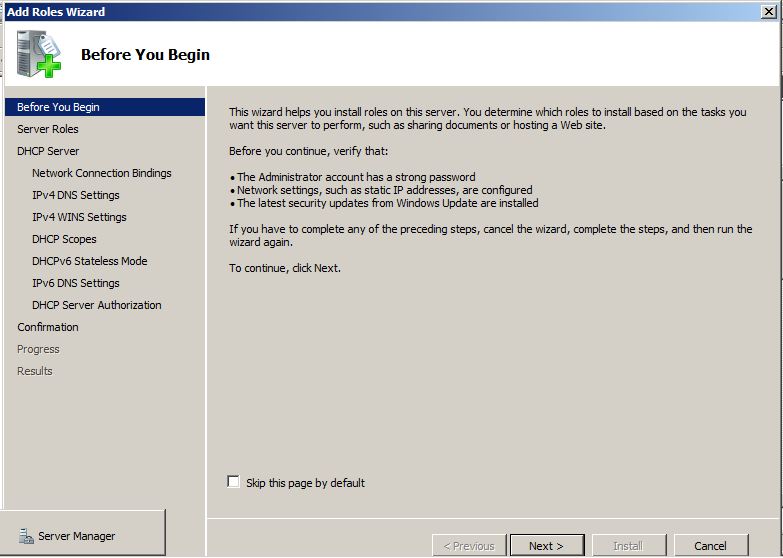
When Windows Server 2008 R2 computer is configured as a DHCP server, it can have multiple NICs and each NIC can be configured to provide IP addresses to the computers that belong to different subnets. For example, if Windows Server 2008 R2 DHCP server has NIC-1 with 192.168.0.22 and NIC -2 with 192.168.1.22 static IP addresses assigned to them, both NICs, if configured appropriately, can provide dynamic IP addresses to the clients connected to their respective subnets.

Computer Training Excuses -

You wouldn't go to a doctor who had never been to medical school, or hire a lawyer who never studied law. One side-effect of a world advancing as rapidly as ours is that fields are becoming more and more specialized and narrow. People can no longer get by on general knowledge in their careers, something I found out for myself not too long ago. I'd been out of high school for two years, scraping by on my own and picking up scraps of programming as I went. I saw all of the self-taught programmers breaking into the IT industry, and I hoped to do the same. After all, IT is one of the few industries out there where being creative and a quick learner is more important than a degree.

Understanding LAN Bridges -

LAN Bridges were used to separate and isolate multiple collision domains from each other in large broadcast domains. Bridges had two or more LAN ports to which other central devices, such as network Hubs, were connected via LAN cables. Unlike network Hubs that used to forward data packets to every PC that was connected to the ports, Bridges acted more like LAN Switches to identify destination ports and transferred the data packets only if the packets were destined to reach the segments that were connected to their other ends. Bridges used to calculate and identify the destination segments on the basis of physical (MAC) addresses of the central devices that were connected to their LAN ports.

Understanding DNS Updates & DNS Records -

DNS records are the objects that are created either manually by the DNS administrators or automatically by the DNS servers themselves. A DNS server can have indefinite numbers of records and each DNS record is helpful in resolving the query of its own type. For example a Host (A) record in DNS server helps resolving a hostname to its corresponding IPv4 address whereas Host (AAAA) record resolves hostname to its corresponding IPv6 addresses.

Understanding Star Topology -

Since over a decade, star topologies have been preferred over bus topologies by the administrators. In star topology, a central device (Hub or Switch) is used to connect multiple PCs in a local area network. Central devices that are used in star topologies have multiple LAN ports integrated in them and the PCs are connected to the central devices via patch cables. In most cases patch cables are twisted pair cables that have four twisted pairs (eight wires in all) which are crimped to the RJ-45 connectors. The reason why star topology is mostly preferred nowadays is that it does not provide a single point of failure and is highly scalable. This means ...

Add New Host (A) Record in W2K8R2 DNS Server -
%20Record.JPG)
In any network setup DNS server plays an important role as it helps client computers to resolve names to their respective IP addresses. When a DNS server is installed in a network it automatically creates a Forward Lookup Zone and adds some records in it by its own. A DNS server can have several record types depending on the type of network.
D-Link Cloud Router DIR-605L -
.png)
This time we had the chance to try out a product from the Chinese firm
D-Link, a renowned manufacturer of computer networking equipment. It is a product that is called
Cloud Router and is classified by the marking
DIR-605L. In the package, next to the router, you get a
voltage adapter (5V DC, 1A),
LAN cable,
CD with instructions and software, as well as printed documentation.

IP Spoofing and Sniffing -
 Sniffing and spoofing
Sniffing and spoofing are security threats that target the lower layers of the
networking infrastructure supporting applications that use the Internet. Users do not interact directly with these lower layers and are typically completely unaware that they exist. Without a deliberate consideration of these threats, it is impossible to build effective security into the higher levels. Sniffing is a passive
security attack in which a machine separate from the intended destination reads data on a network. The term
"sniffing" comes from the notion of
"sniffing the ether" in an
Ethernet network and is a bad pun on the two meanings of the word
"ether." Passive
security attack are those that do not alter the normal flow of data on a communication link or inject data into the link.
Internet Backbone Speeds -
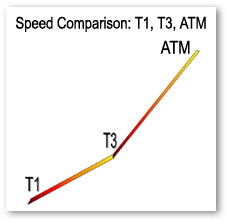
This is something that can come in handy for those of you who are simply curious about internet backbone speeds.
Understading Networking Hubs -

Network hubs were the central devices that network administrators used to use to establish a network setup using Star Topologies. Network hubs had multiple RJ-45 ports integrated in them and were used to connect one end of the LAN cables that had RJ-45 connectors crimped to them. The other end of the cables were connected to the RJ-45 ports available on the PCs. Network hubs were available with 4, 8, 16 and 24 ports. Administrators also used to cascade two hubs for larger network setups. Cascading means that one RJ-45 port of one hub connected to ...

Understanding Routers -

Routers are the devices that are used to connect two different networks in order to allow communication between them. Networks with different network IDs are considered to be different. By default, no communication can take place between two different networks, and this configuration prevents computers of one network from getting accessed by the computers on the other network, which may belong to another organization, building premises, home, etc.

How to Enable Remote Desktop in Windows Server 2008 R2 -
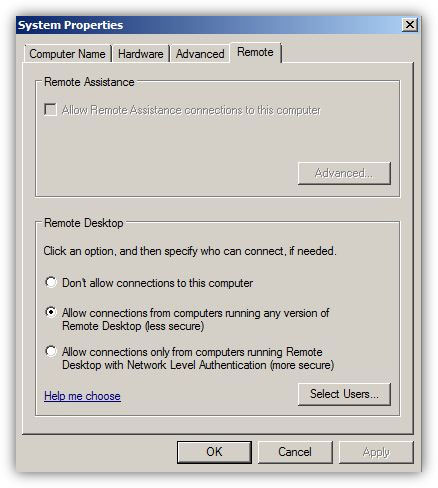
The concept of Remote Desktop was first introduced with the release of Microsoft Windows 2000 (Professional and Server editions) which was then carried forward to all the successor versions of Microsoft-based operating systems. With the help of Remote Desktop administrators can manage remote computers by bringing their entire consoles on the local computer from where they have initiated the Remote Desktop sessions. By using Remote Desktop administrators can administer remote computers as easily and comfortably as they were physically present in front of the remote computers and were locally logged on to them. Since Remote Desktop allows administrators to manage multiple remote machines from single central location, it saves a decent amount of time that administrators would otherwise had to spend if there was no Remote Desktop feature available in the operating systems.

Understanding Collision and Broadcast Domains -

In computer networks, scope (area) up to where data that is transferred over the cables or the wireless media with certain conditions is categorized in two domain main types. In complex network setups, because multiple segments are connected to each other via different types of central devices, it becomes important for the administrators to separate broadcast domains and reduce the numbers of collision domains. A central device in which collisions may occur is Hub because of it logical Bus Topology.
Understanding DNS Zones -

When a DNS server role is installed on a network operating system, by default forward lookup zone is automatically created and the DNS server works as Caching Only server that caches the results of all the queries that it resolves. Forward lookup zone of a DNS server resolves IP addresses to their corresponding host names, is used in most network setups in production environments.

IT College Program vs. IT Boot Camp -

Perhaps it is time for a career change, or you are fresh out of high school and the idea of four more years of schooling does not appeal to you. After much research you have decided to embark upon a career in the Information Technology field. Not a bad choice, especially since Technology changes every day.
You are faced with the choice of education. As previously stated, going to
computer school for four years to get a
computer science degree is not an option but there is another option,
IT Boot Camp. And
IT Boot Camps solely focus on a very limited number of IT Certifications. So there can be
MCSE Boot Camps that may focus on just that.
What to Expect at the Testing Center -

In order to do their best, candidates should know what to expect at the testing center for the Cisco CCNA certification exam. Read for more information.
How to Share Printer in Windows Server 2008 R2 -
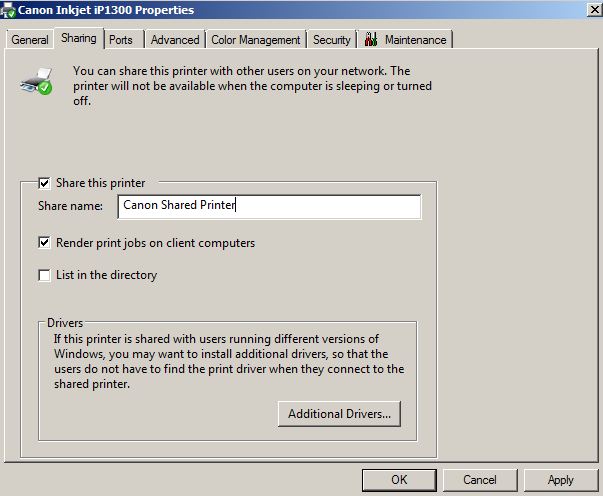
Just like folder sharing in Microsoft Windows operating systems, printer sharing is also an important part in any complex network setup or in simple networking in homes. In either case mostly one printing device is bought and is shared among all the computers connected to the network. Since printing devices, sometimes, are expensive sharing them among all computers in networks is a cost effective approach for both administrators and home users.
Cisco Certified Network Associate (CCNA) Exam: 640-607 -

This tutorial will most definitely be the only thing you need to get by CCNA. That doesn't mean that there is no need to study with other resources as we feel the more hard work put in the better. But skim through this tutorial and see for yourself. It just might be your last stop to CCNA training.
Start-Up's True Tale -

Often-told story of Cisco's launch leaves out the drama and intrigue...Founding legends are a specialty of Silicon Valley, and none is more appealing than that of Cisco Systems: i/In the 1980s a young Stanford University couple invent the multiprotocol router and starts Cisco in their living room, using their own credit cards for financing.
Understanding DHCP Classes -

In small-scale organizations and home environments, DHCP servers are installed normally and no class oriented configurations are done. The reason behind this is that by default all DHCP client computers belong to default DHCP class and as soon as DHCP scopes are configured and the DHCP servers become ready to assign dynamic addresses to the client computers, the DHCP clients start receiving the IP addresses without any additional administrative overheads. However, in order to allow DHCP servers to assign different ...
Understanding DHCP Servers -

Dynamic Host Configuration Protocol or DHCP servers are the dedicated computers that have network operating systems installed on them and are responsible for providing automatic IP addresses to all the client computers that are configured to obtain the addresses automatically.
TW Tech Glossary - Misplaced your bible? Well here it is - Tech Glosasary! This truly took a while to complete and should be used by all from beginners to advance techies.
IT Certifications a Solid Return On Investment -

Step into the realm of IT Certifications. Where millions have entered and zillions have flunked. Ah, that didnt sound right, mathematically speaking that is. Anyway, if your one of the few breeds that like to get your hands on a certification and get ahead in your work place, it is strongly recommended that you read this article. Its not made with grueling details and gets right down to the point. So check it out, you probably owe it to yourself by now!
Beginner Computer Training FAQ -

Use the webs best resource to find computer and technical training schools near you. Choose from hundreds of schools offering Classroom, Corporate, Onsite, and Online programs.
Assigning Multiple DNS IP Addresses on Windows Server 2008 R2 -
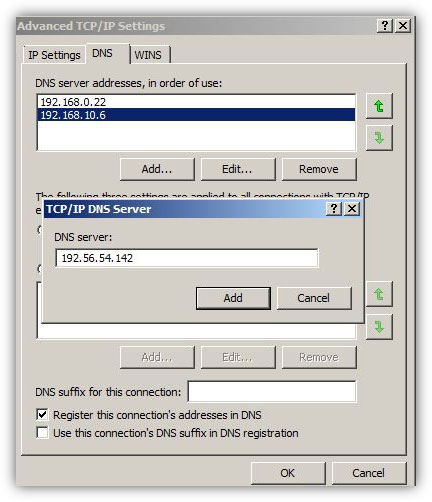
In medium or large-scale organizations where there are several client computers connected to a network, administrators install multiple DNS servers in order to load balance the traffic and to reduce the burden on a single DNS server. Moreover, if there are multiple DNS servers configured in such network scenarios it is likely that administrators might have configured one DNS server as DNS forwarder and have configured other DNS servers to forward the queries to the forwarder. This is an efficient approach that almost all administrators take for error free and smooth name resolution process.

Understanding LAN Switches -

LAN switches, which are also sometimes called intelligent hubs, are the networking devices that have completely dominated and replaced Hubs. The reason behind this is that unlike Hubs, that only used to regenerate the received packets and forward them to all the ports that they had, LAN switches create one-to-one virtual circuits directly to the ports to which the destination computers are connected. This reduces the time consumed while transferring the data packets from the source computers to the destination ones.
How to Map Network Drive in Windows Server 2008 R2 -
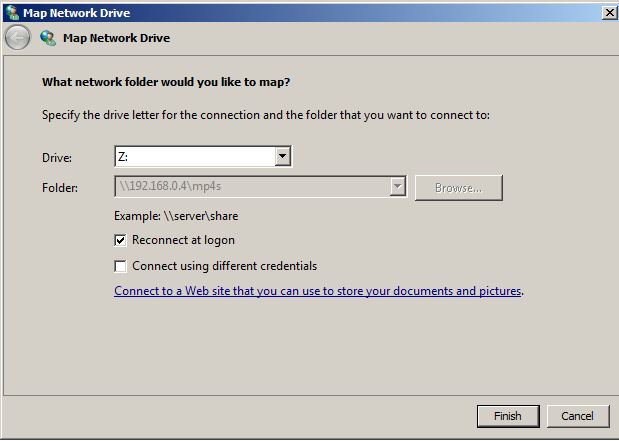
Network drive mapping is a process in which users create shortcuts of shared folders on their local computers. Shared folders can be located anywhere in the network. Shortcuts that users create appear in Computer (in Windows Vista and above operating systems) and My Computer (in pre-Windows Vista operating systems) window.

Understanding Wireless Network Topologies -

In any network setup, network topology plays an important role without which network cannot be established whatsoever. In other words, whenever two or more machines are connected to each other, a topology is automatically formed. Unlike wired networks that have multiple topologies, wireless networks have only two topologies namely Infrastructure and Ad Hoc. Since wireless networks work on unguided media, it makes sense to have limited number of topologies while configuring the wireless network setups. Moreover, since wireless networks are a bit complicated configure as compared to the wired networks, it is essential for the administrators to have ...

Understanding Ring Topology -

In ring topology, data used to transfer in the form of ring where every computer that was connected to the network had two LAN cards and each LAN card was connected to the LAN card of its neighbor computer. Many times ring topology was preferred over bus topology because there were no collisions and the chances of network getting congested were next to 0%.
Selecting the Best Computer Science Field -

If you are looking for career counseling, and are in a dilemma as which branch of computer science you should go for, this small section would hopefully help you in selecting the best option according to your nature and interest. In computer industry, there are several branches from which you can choose any one. The reason behind this is that in this industry, you can get success and/or fame only when you are skilled, and full of knowledge.

Getting Into IT - No Experience No Qualification -
 But how?
But how? If you have computer skill but no experience (
or qualifications), the employment agencies will tell you the same old line,
"You need experience before anyone will look at you."
It's just plain old Catch-22. You need the work to get the experience but you can't get that first job to give you a track record and therefore verifiable experience. With this logic, it amazes me that anyone actually gets into IT!
Qualifications help but even that is no guarantee nowadays of getting an IT Job. And what do you do when you don't have qualifications but you want to start now? I mean right now, not 3 months later after you've paid a fortune for certification and given up your job to have enough study time.
All is not lost. You have two alternatives.

What REAL Computer People Need To Know -

A great deal of fundamental understanding about computers has been mostly lost from our world today. Computers are so complicated and work so reliably nowadays that many of the finer aspects of computing are now little more than dim memories in the minds of some older hackers, or little-read publications gathering dust in libraries somewhere. People often try to get away with knowing as little as they can, and while they might be able to get away with that, it's distressing how many people who believe themselves to be knowledgeable about computers are actually unaware of some highly fundamental concepts.

How to Promote Windows Server 2008 R2 to a Domain Controller -
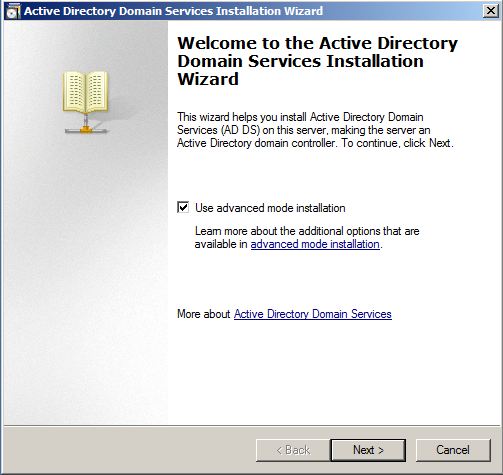
In Microsoft Windows platform all post-Windows 2000 Server network operating systems are shipped along with built-in Active Directory Services (ADS in Windows Server 2003) or Active Directory Domain Services (AD DS in Windows Server 2008) which differentiates them from client operating systems. Although the services are integrated in the network operating systems, they are not automatically installed during the installation of the OS. Because of this when a network operating system is installed on a computer it works as a client operating system and is technically called a ...

Understanding Bus Topology -

n a nutshell, network topologies are the physical alignments of computers and the way they are connected to each other. For example, if all the computers are connected to each other via a central device (Hub or Switch), the type of topology is Star. Likewise, if all the computers are connected to each other via a main cable, this means it is Bus Topology.
What is CCNA?
 As Cisco mentions on thier website, the CCNA certification (Cisco Certified Network Associate) indicates a foundation in and apprentice knowledge of networking. CCNA certified professionals can install, configure, and operate LAN, WAN, and dial access services for small networks (100 nodes or fewer), including but not limited to use of these protocols: IP, IGRP, Serial, Frame Relay, IP RIP, VLANs, RIP, Ethernet, Access Lists.
As Cisco mentions on thier website, the CCNA certification (Cisco Certified Network Associate) indicates a foundation in and apprentice knowledge of networking. CCNA certified professionals can install, configure, and operate LAN, WAN, and dial access services for small networks (100 nodes or fewer), including but not limited to use of these protocols: IP, IGRP, Serial, Frame Relay, IP RIP, VLANs, RIP, Ethernet, Access Lists.
Exam Details:
Exam Number: 640-607
Associated Certifications: CCNA
Duration: 75 min (45-55 questions)
Available Languages: English, Japanese in Japan only
Please Note: The Cisco Certified Network Associate exam (CCNA) is the only exam required to achieve a CCNA Routing and Switching certification.
Topics Covered:
Bridging/Switching
- Distinguish between cut-through and store-and-forward LAN switching
- Describe the operation of the Spanning Tree Protocol and its benefits
- Verify the operation of the Spanning Tree Protocol on the switch
- Describe the operation and benefits of VLANs
- Configure VLANs on a switch
- Configure VTP and trunking on switches
- Compare and contrast switches and bridges
- Identify anomolies in VLAN, trunking, and VTP operation
- Configure a switch for basic operations
OSI Reference Model & Layered Communication
- Describe data link and network addresses and identify key differences between them
- Identify at least three reasons why the industry uses a layered model
- Define and explain the conversion steps of data encapsulation and de-encapsulation
- Describe connection-oriented network service and connectionless network service, and identify their key differences
- Describe the functions of each the seven layers of the OSI model and their corresponding applications
- Compare the OSI model with the TCP/IP stack
- Match networking devices to their OSI layer(s)
- Use the OSI model as a conceptual strategy to identify network problems
Routed Protocols
- Describe the different classes of IP addresses including subnetting and private addresses
- Configure IP addresses
- Troubleshoot IP address schemes
- Develop an IP addressing scheme to meet requirements
- Identify the fundamental uses of various TCP/IP application layer protocols
- Convert between decimal, hexadecimal, and binary
- Define flow control and describe the three basic methods used in networking
- Explain the functions of the TCP/IP network and transport layer protocols
Routing Protocols
- Configure a router for inter-VLAN communication
- Verify IP routing with show and debug commands
- Compare and contrast the key operations that distinguish distance-vector, link-state, and hybrid protocols
- Identify exterior and interior routing protocols
- Configure static and default routes on a router
- Enable RIP and IGRP on a router
- Identify routing metrics used by IGRP and RIP
WAN Protocols
- Explain key Frame Relay terms and features
- Configure Frame Relay LMIs, maps, and subinterfaces
- Identify ISDN protocols, function groups, reference points, and channels
- Differentiate between the following WAN services: LAPB, Frame Relay, ISDN/LAPD, HDLC, PPP, and DDR
- Identify PPP operations to encapsulate WAN data on Cisco routers
- Use show commands to display network operational parameters so that anomalies are detected
- Configure ISDN BRI and legacy dial-on-demand routing (DDR)
- Configure a serial connection with PPP encapsulation
Network Management
- Monitor and verify selected access list operations on the router
- Configure authentification types (CHAP/PAP) on PPP links
- Manage configuration files from the privilege EXEC mode
- Manage IOS images and device configuration files
- Load Cisco IOS software from: Flash memory, a TFTP server, or ROM
- Perform backup, upgrade, and loading of Cisco IOS software and configuration files
- Configure access lists to meet specified operational requirements
- Use CDP to identify a network topology
- Use ICMP to verify network connectivity and locate network problems
LAN Technologies
- Determine the appropriate uses for full- and half-duplex Ethernet operation.
- Describe the causes and effects of network congestion in Ethernet networks
- Describe the benefits of network segmentation with various networking devices
- Identify the cause(s) of LAN connectivity problem
- Describe the function, operation, and primary components on a LAN
Cisco Basics, IOS & Network Basics
- Describe router elements (RAM, ROM, Flash, NVRAM, config register)
- Configure router passwords, identification, and banner
- Use the context-sensitive help facility
- Use the command history and editing features
- Perform the initial router configuration (including using the setup mode).
- Use show commands to display basic network operational parameters
- Describe router start-up sequence
- Establish connectivity from a host to the appropriate network device to perform configuration tasks
- In accordance with open standards, interconnect network devices
- Differentiate between routed and routing protocols
Tips
CCNA Cisco Certification Tip
- The layer in OSI reference model communicates with each other using protocol data units ( PDUs).
- Hub is a physical layer device and it is concerned only with propagation of the physical signaling without any regard for upper -layer functions.
- Logical link control (LLC) sublayer (802.2) is responsible for logically identifying different protocol types and then encapsulating them in order to be transmitted across the network.
- A Bridge learns all the station destinations by listening to source addresses so it never learns the broadcast address.
- A network address is protocol-specific. If a router supports more than one protocol, it will have a unique table for each protocol.
- Metric in routers refers to the cost or distances to the target network. This is a value that helps the router choose the best path to a given network. This metric changes depending on how the router chooses paths.
- The term Ethernet refers to a family of LAN implementations. Physical layer implementations vary and all support various media types.
- A cross over cable crosses the critical pairs in order to properly align, transmit and receive signals on devices with like connectors.
- For connection between similar devices such as DCE to DCE, DTE to DTE, crossover cable is used. Whereas, for connecting dissimilar devices such as DCE to DTE, straight cable is used.
- BRI-S/T port is used when NT1 is provided separately. BRI-U port is used when built in NT1 is used.
- The AUX port provided on some devices can be used to provide out-of-band management via a modem. The AUX port must be configured using the console port before it can be used.
- When Cisco router is started for the first time, it does not have any initial configuration.
- During LED/POST Test, if LED 4x (console port) fails, then you cannot access the management console through the console port, but you can still Telnet to the management console.
- A question mark (?) during the EXEC session will always provide help.
- The configuration changes to the switch are immediate. As soon as you press `Return` in any configuration mode, the parameter has been changed and the action executes in running memory.
- Commands in the CISCO IOS can be abbreviated by entering enough of the command to be unique.
- By default, command history is enabled and the system records ten commands line in the history buffer.
- The commands `write term` and `show config` used with CISCO IOS release 10.3 and earlier have been replaced by new commands, but continue to perform their normal functions.
- If you type `Exit` in the router mode, the router will back out one level, eventually allowing you to log out.
- Logging synchronous console line command line is useful whenever console messages are being displayed at the same time that you are attempting to input EXEC or configuration command.
- Serial links have two sides. One side of the link is responsible for clocking and is called a DCE.
- CDP functionality is enabled by default on all interfaces.
- Some CISCO devices such as the catalyst 1900 switches don't support the telnet command.
- The ping command (packet internet gropper) verifies connectivity.
- When a configuration is copied into RAM from any source, the configuration merges with, or overlays, any existing configuration in RAM rather then overwriting it.
- Layer 2 switches have three major functions: address learning, packet forwarding / filtering and loop avoidance.
- The purpose of the spanning-Tree protocol is to maintain a loop-fee network. Spanning Tree protocol is enabled by default in catalyst switches.
- To make a bridge as Root Bridge, its priority should be lowered.
- On the catalyst 1900 switch, the running configuration is automatically saved to NVRAM whenever a change is made to the running configuration.
- Though VLANs are a layer 2 implementation in the switch fabric but they are protocol independent.
- ARP is used to resolve or map a known destination IP address to a MAC sublayer address to allow communication on a multi-access medium such as Ethernet.
- The static route is configured for connectivity to a data link not directly connected to your routes. For end-to-end connectivity a route must be configured in both directions.
- Administrative distance value is used to rate the trustworthiness of each routing source.
- The rule of split horizon is that it is never useful to send information about a route back in the direction from which the original update came.
- The 'show ip protocols' command displays values associated with routing timers and network information associated with the entire router.
- By defaults only bandwidth and delay are used by IGRP metric.
- All routers within an autonomous system must use the same autonomous number, or they will not exchange routing information.
- With 'ip classless' configured, if a packet is received with a destination address within an unknown subnet of a directly attached network, the router will match it to the default route and forward it to the next hop specified by the default route.
- Access lists identify traffic to be filtered in the transit through the router, but they do not filter traffic that originated from the router.
- Because of the implicit deny any, an access list should have at least one permit statement in it, otherwise the access test will block all traffic.
- An access list can be applied to multiple interfaces. However there can be only one access list per protocol, per direction, per interface.
- Access lists are processed from the top down. If you place more specific tests and tests that will test true frequently in the beginning of the access list, you can reduce processing overhead.
- A Novell IPX address has 80 bits - 32 bits for the network number and 48 bits for the node number. It is expressed as a hexadecimal number.
- Cisco IPX echoes are used to ping between Cisco routers to verify connectivity and are not compatible with Novell IPX pings, which can be used to ping between servers.
- Customer premises equipment is always the data terminal equipment (DTE). DCE provides the clock and DTE needs external clock.
- Cisco's HDLC is a point to point protocol that can be used on leased lines between two devices supporting Cisco proprietary HDLC encapsulation. If communicating with a non-Cisco device, synchronous PPP is a more viable option.
- While configuring PPP authentication, configure interface first and then router for password and username.
- While configuring PAP or CHAP on Cisco router the password must be the same for both routers.
- If both PAP and CHAP are configured, the one that is listed first in the PPP authentication interface configuration command is tried first.
- The D channel between the router and the ISDN switch is always up. When the call is initiated the called number is sent to the local ISDN switch. The D channel is used for call setup, signaling and call termination.
|
|
|
|
 Did You Know?
- MCSE is the number 1 certificate that most people are trying to land on within the next 2 years.
- Cisco certifications are the MOST popluar amongst all networking certifications.

|
|
|
|
|
|












































 As Cisco mentions on thier website, the CCNA certification (Cisco Certified Network Associate) indicates a foundation in and apprentice knowledge of networking. CCNA certified professionals can install, configure, and operate LAN, WAN, and dial access services for small networks (100 nodes or fewer), including but not limited to use of these protocols: IP, IGRP, Serial, Frame Relay, IP RIP, VLANs, RIP, Ethernet, Access Lists.
As Cisco mentions on thier website, the CCNA certification (Cisco Certified Network Associate) indicates a foundation in and apprentice knowledge of networking. CCNA certified professionals can install, configure, and operate LAN, WAN, and dial access services for small networks (100 nodes or fewer), including but not limited to use of these protocols: IP, IGRP, Serial, Frame Relay, IP RIP, VLANs, RIP, Ethernet, Access Lists.
 In this article, we would like to point out the obvious IT Jobs that at times get overlooked. Find out what's out there and which information technology is the right choice for you. From people that create laptop computers to folks that do web design to developers that come up with computer software concepts from scratch. Also a bit at the end about
In this article, we would like to point out the obvious IT Jobs that at times get overlooked. Find out what's out there and which information technology is the right choice for you. From people that create laptop computers to folks that do web design to developers that come up with computer software concepts from scratch. Also a bit at the end about  We all know that we need more bandwidth now, than we ever did in the past. There tons more online games, online movies, online collab work, you name it. And the past standards of Wifi namely 802.11a, 802.11b, 802.11g, 802.11n, and so on) were getting better and better; however, the 802.11ac does the trick. Well, atleast for now it is, until something better comes along.
We all know that we need more bandwidth now, than we ever did in the past. There tons more online games, online movies, online collab work, you name it. And the past standards of Wifi namely 802.11a, 802.11b, 802.11g, 802.11n, and so on) were getting better and better; however, the 802.11ac does the trick. Well, atleast for now it is, until something better comes along. Domain Name System or DNS servers are dedicated computers that have network operating systems installed on them and are responsible for resolving hostnames (computer names) to their IP addresses and vice versa. DNS servers are used worldwide and are helpful while accessing the Internet and visiting websites. Every Internet Service Provider or ISP has its own DNS server which receives name resolution requests from the subscribers of that ISP and resolves the requested host names to their corresponding IP addresses.
Domain Name System or DNS servers are dedicated computers that have network operating systems installed on them and are responsible for resolving hostnames (computer names) to their IP addresses and vice versa. DNS servers are used worldwide and are helpful while accessing the Internet and visiting websites. Every Internet Service Provider or ISP has its own DNS server which receives name resolution requests from the subscribers of that ISP and resolves the requested host names to their corresponding IP addresses. Apart from star topology that is widely used in almost every network environment, the other type of topology that is complex while setting up but provides 100% fault tolerance to the network is Mesh Topology. In this topology, every computer that has to be connected to the network is connected to every computer that is available in the network. For example if there are four computers namely A, B, C and D, then A will be connected to B, C and D. Likewise B will be connected to A, C and D and so on. This means that when mesh topology is used while establishing a network setup, it is very unlikely that the network would ever face congestions or would ever fail.
Apart from star topology that is widely used in almost every network environment, the other type of topology that is complex while setting up but provides 100% fault tolerance to the network is Mesh Topology. In this topology, every computer that has to be connected to the network is connected to every computer that is available in the network. For example if there are four computers namely A, B, C and D, then A will be connected to B, C and D. Likewise B will be connected to A, C and D and so on. This means that when mesh topology is used while establishing a network setup, it is very unlikely that the network would ever face congestions or would ever fail. In organizations or home setups where there are multiple computers connected to each other, in order to transfer files from one computer to another administrators use to share the folders on one computer (generally known as file server) and make them accessible from all other computers in the network. In order to do so administrators normally configure and set NTFS and share permissions on the shared folders which, as a result, help them control the accessibility of user accounts or groups on them.
In organizations or home setups where there are multiple computers connected to each other, in order to transfer files from one computer to another administrators use to share the folders on one computer (generally known as file server) and make them accessible from all other computers in the network. In order to do so administrators normally configure and set NTFS and share permissions on the shared folders which, as a result, help them control the accessibility of user accounts or groups on them. One of most important type of server is cluster servers. Software that enables clustering of servers is installed into a computer. Clustering servers also serve as load balancing servers between two computers. This is a common small business server. Clustering servers are used to avoid server failover. Server failover is the capability to shift to another standby server if the main server fails.
One of most important type of server is cluster servers. Software that enables clustering of servers is installed into a computer. Clustering servers also serve as load balancing servers between two computers. This is a common small business server. Clustering servers are used to avoid server failover. Server failover is the capability to shift to another standby server if the main server fails. You wouldn't go to a doctor who had never been to medical school, or hire a lawyer who never studied law. One side-effect of a world advancing as rapidly as ours is that fields are becoming more and more specialized and narrow. People can no longer get by on general knowledge in their careers, something I found out for myself not too long ago. I'd been out of high school for two years, scraping by on my own and picking up scraps of programming as I went. I saw all of the self-taught programmers breaking into the IT industry, and I hoped to do the same. After all, IT is one of the few industries out there where being creative and a quick learner is more important than a degree.
You wouldn't go to a doctor who had never been to medical school, or hire a lawyer who never studied law. One side-effect of a world advancing as rapidly as ours is that fields are becoming more and more specialized and narrow. People can no longer get by on general knowledge in their careers, something I found out for myself not too long ago. I'd been out of high school for two years, scraping by on my own and picking up scraps of programming as I went. I saw all of the self-taught programmers breaking into the IT industry, and I hoped to do the same. After all, IT is one of the few industries out there where being creative and a quick learner is more important than a degree. LAN Bridges were used to separate and isolate multiple collision domains from each other in large broadcast domains. Bridges had two or more LAN ports to which other central devices, such as network Hubs, were connected via LAN cables. Unlike network Hubs that used to forward data packets to every PC that was connected to the ports, Bridges acted more like LAN Switches to identify destination ports and transferred the data packets only if the packets were destined to reach the segments that were connected to their other ends. Bridges used to calculate and identify the destination segments on the basis of physical (MAC) addresses of the central devices that were connected to their LAN ports.
LAN Bridges were used to separate and isolate multiple collision domains from each other in large broadcast domains. Bridges had two or more LAN ports to which other central devices, such as network Hubs, were connected via LAN cables. Unlike network Hubs that used to forward data packets to every PC that was connected to the ports, Bridges acted more like LAN Switches to identify destination ports and transferred the data packets only if the packets were destined to reach the segments that were connected to their other ends. Bridges used to calculate and identify the destination segments on the basis of physical (MAC) addresses of the central devices that were connected to their LAN ports. Since over a decade, star topologies have been preferred over bus topologies by the administrators. In star topology, a central device (Hub or Switch) is used to connect multiple PCs in a local area network. Central devices that are used in star topologies have multiple LAN ports integrated in them and the PCs are connected to the central devices via patch cables. In most cases patch cables are twisted pair cables that have four twisted pairs (eight wires in all) which are crimped to the RJ-45 connectors. The reason why star topology is mostly preferred nowadays is that it does not provide a single point of failure and is highly scalable. This means ...
Since over a decade, star topologies have been preferred over bus topologies by the administrators. In star topology, a central device (Hub or Switch) is used to connect multiple PCs in a local area network. Central devices that are used in star topologies have multiple LAN ports integrated in them and the PCs are connected to the central devices via patch cables. In most cases patch cables are twisted pair cables that have four twisted pairs (eight wires in all) which are crimped to the RJ-45 connectors. The reason why star topology is mostly preferred nowadays is that it does not provide a single point of failure and is highly scalable. This means ....png) This time we had the chance to try out a product from the Chinese firm D-Link, a renowned manufacturer of computer networking equipment. It is a product that is called Cloud Router and is classified by the marking DIR-605L. In the package, next to the router, you get a voltage adapter (5V DC, 1A), LAN cable, CD with instructions and software, as well as printed documentation.
This time we had the chance to try out a product from the Chinese firm D-Link, a renowned manufacturer of computer networking equipment. It is a product that is called Cloud Router and is classified by the marking DIR-605L. In the package, next to the router, you get a voltage adapter (5V DC, 1A), LAN cable, CD with instructions and software, as well as printed documentation. Sniffing and spoofing are security threats that target the lower layers of the
Sniffing and spoofing are security threats that target the lower layers of the  This is something that can come in handy for those of you who are simply curious about internet backbone speeds.
This is something that can come in handy for those of you who are simply curious about internet backbone speeds. Network hubs were the central devices that network administrators used to use to establish a network setup using Star Topologies. Network hubs had multiple RJ-45 ports integrated in them and were used to connect one end of the LAN cables that had RJ-45 connectors crimped to them. The other end of the cables were connected to the RJ-45 ports available on the PCs. Network hubs were available with 4, 8, 16 and 24 ports. Administrators also used to cascade two hubs for larger network setups. Cascading means that one RJ-45 port of one hub connected to ...
Network hubs were the central devices that network administrators used to use to establish a network setup using Star Topologies. Network hubs had multiple RJ-45 ports integrated in them and were used to connect one end of the LAN cables that had RJ-45 connectors crimped to them. The other end of the cables were connected to the RJ-45 ports available on the PCs. Network hubs were available with 4, 8, 16 and 24 ports. Administrators also used to cascade two hubs for larger network setups. Cascading means that one RJ-45 port of one hub connected to ... Routers are the devices that are used to connect two different networks in order to allow communication between them. Networks with different network IDs are considered to be different. By default, no communication can take place between two different networks, and this configuration prevents computers of one network from getting accessed by the computers on the other network, which may belong to another organization, building premises, home, etc.
Routers are the devices that are used to connect two different networks in order to allow communication between them. Networks with different network IDs are considered to be different. By default, no communication can take place between two different networks, and this configuration prevents computers of one network from getting accessed by the computers on the other network, which may belong to another organization, building premises, home, etc. In computer networks, scope (area) up to where data that is transferred over the cables or the wireless media with certain conditions is categorized in two domain main types. In complex network setups, because multiple segments are connected to each other via different types of central devices, it becomes important for the administrators to separate broadcast domains and reduce the numbers of collision domains. A central device in which collisions may occur is Hub because of it logical Bus Topology.
In computer networks, scope (area) up to where data that is transferred over the cables or the wireless media with certain conditions is categorized in two domain main types. In complex network setups, because multiple segments are connected to each other via different types of central devices, it becomes important for the administrators to separate broadcast domains and reduce the numbers of collision domains. A central device in which collisions may occur is Hub because of it logical Bus Topology. Perhaps it is time for a career change, or you are fresh out of high school and the idea of four more years of schooling does not appeal to you. After much research you have decided to embark upon a career in the Information Technology field. Not a bad choice, especially since Technology changes every day.
You are faced with the choice of education. As previously stated, going to computer school for four years to get a computer science degree is not an option but there is another option, IT Boot Camp. And IT Boot Camps solely focus on a very limited number of IT Certifications. So there can be MCSE Boot Camps that may focus on just that.
Perhaps it is time for a career change, or you are fresh out of high school and the idea of four more years of schooling does not appeal to you. After much research you have decided to embark upon a career in the Information Technology field. Not a bad choice, especially since Technology changes every day.
You are faced with the choice of education. As previously stated, going to computer school for four years to get a computer science degree is not an option but there is another option, IT Boot Camp. And IT Boot Camps solely focus on a very limited number of IT Certifications. So there can be MCSE Boot Camps that may focus on just that. In order to do their best, candidates should know what to expect at the testing center for the Cisco CCNA certification exam. Read for more information.
In order to do their best, candidates should know what to expect at the testing center for the Cisco CCNA certification exam. Read for more information. This tutorial will most definitely be the only thing you need to get by CCNA. That doesn't mean that there is no need to study with other resources as we feel the more hard work put in the better. But skim through this tutorial and see for yourself. It just might be your last stop to CCNA training.
This tutorial will most definitely be the only thing you need to get by CCNA. That doesn't mean that there is no need to study with other resources as we feel the more hard work put in the better. But skim through this tutorial and see for yourself. It just might be your last stop to CCNA training. Often-told story of Cisco's launch leaves out the drama and intrigue...Founding legends are a specialty of Silicon Valley, and none is more appealing than that of Cisco Systems: i/In the 1980s a young Stanford University couple invent the multiprotocol router and starts Cisco in their living room, using their own credit cards for financing.
Often-told story of Cisco's launch leaves out the drama and intrigue...Founding legends are a specialty of Silicon Valley, and none is more appealing than that of Cisco Systems: i/In the 1980s a young Stanford University couple invent the multiprotocol router and starts Cisco in their living room, using their own credit cards for financing. In small-scale organizations and home environments, DHCP servers are installed normally and no class oriented configurations are done. The reason behind this is that by default all DHCP client computers belong to default DHCP class and as soon as DHCP scopes are configured and the DHCP servers become ready to assign dynamic addresses to the client computers, the DHCP clients start receiving the IP addresses without any additional administrative overheads. However, in order to allow DHCP servers to assign different ...
In small-scale organizations and home environments, DHCP servers are installed normally and no class oriented configurations are done. The reason behind this is that by default all DHCP client computers belong to default DHCP class and as soon as DHCP scopes are configured and the DHCP servers become ready to assign dynamic addresses to the client computers, the DHCP clients start receiving the IP addresses without any additional administrative overheads. However, in order to allow DHCP servers to assign different ... Step into the realm of IT Certifications. Where millions have entered and zillions have flunked. Ah, that didnt sound right, mathematically speaking that is. Anyway, if your one of the few breeds that like to get your hands on a certification and get ahead in your work place, it is strongly recommended that you read this article. Its not made with grueling details and gets right down to the point. So check it out, you probably owe it to yourself by now!
Step into the realm of IT Certifications. Where millions have entered and zillions have flunked. Ah, that didnt sound right, mathematically speaking that is. Anyway, if your one of the few breeds that like to get your hands on a certification and get ahead in your work place, it is strongly recommended that you read this article. Its not made with grueling details and gets right down to the point. So check it out, you probably owe it to yourself by now! Use the webs best resource to find computer and technical training schools near you. Choose from hundreds of schools offering Classroom, Corporate, Onsite, and Online programs.
Use the webs best resource to find computer and technical training schools near you. Choose from hundreds of schools offering Classroom, Corporate, Onsite, and Online programs. LAN switches, which are also sometimes called intelligent hubs, are the networking devices that have completely dominated and replaced Hubs. The reason behind this is that unlike Hubs, that only used to regenerate the received packets and forward them to all the ports that they had, LAN switches create one-to-one virtual circuits directly to the ports to which the destination computers are connected. This reduces the time consumed while transferring the data packets from the source computers to the destination ones.
LAN switches, which are also sometimes called intelligent hubs, are the networking devices that have completely dominated and replaced Hubs. The reason behind this is that unlike Hubs, that only used to regenerate the received packets and forward them to all the ports that they had, LAN switches create one-to-one virtual circuits directly to the ports to which the destination computers are connected. This reduces the time consumed while transferring the data packets from the source computers to the destination ones. In any network setup, network topology plays an important role without which network cannot be established whatsoever. In other words, whenever two or more machines are connected to each other, a topology is automatically formed. Unlike wired networks that have multiple topologies, wireless networks have only two topologies namely Infrastructure and Ad Hoc. Since wireless networks work on unguided media, it makes sense to have limited number of topologies while configuring the wireless network setups. Moreover, since wireless networks are a bit complicated configure as compared to the wired networks, it is essential for the administrators to have ...
In any network setup, network topology plays an important role without which network cannot be established whatsoever. In other words, whenever two or more machines are connected to each other, a topology is automatically formed. Unlike wired networks that have multiple topologies, wireless networks have only two topologies namely Infrastructure and Ad Hoc. Since wireless networks work on unguided media, it makes sense to have limited number of topologies while configuring the wireless network setups. Moreover, since wireless networks are a bit complicated configure as compared to the wired networks, it is essential for the administrators to have ... In ring topology, data used to transfer in the form of ring where every computer that was connected to the network had two LAN cards and each LAN card was connected to the LAN card of its neighbor computer. Many times ring topology was preferred over bus topology because there were no collisions and the chances of network getting congested were next to 0%.
In ring topology, data used to transfer in the form of ring where every computer that was connected to the network had two LAN cards and each LAN card was connected to the LAN card of its neighbor computer. Many times ring topology was preferred over bus topology because there were no collisions and the chances of network getting congested were next to 0%. If you are looking for career counseling, and are in a dilemma as which branch of computer science you should go for, this small section would hopefully help you in selecting the best option according to your nature and interest. In computer industry, there are several branches from which you can choose any one. The reason behind this is that in this industry, you can get success and/or fame only when you are skilled, and full of knowledge.
If you are looking for career counseling, and are in a dilemma as which branch of computer science you should go for, this small section would hopefully help you in selecting the best option according to your nature and interest. In computer industry, there are several branches from which you can choose any one. The reason behind this is that in this industry, you can get success and/or fame only when you are skilled, and full of knowledge. But how? If you have computer skill but no experience (or qualifications), the employment agencies will tell you the same old line, "You need experience before anyone will look at you."
But how? If you have computer skill but no experience (or qualifications), the employment agencies will tell you the same old line, "You need experience before anyone will look at you."
 A great deal of fundamental understanding about computers has been mostly lost from our world today. Computers are so complicated and work so reliably nowadays that many of the finer aspects of computing are now little more than dim memories in the minds of some older hackers, or little-read publications gathering dust in libraries somewhere. People often try to get away with knowing as little as they can, and while they might be able to get away with that, it's distressing how many people who believe themselves to be knowledgeable about computers are actually unaware of some highly fundamental concepts.
A great deal of fundamental understanding about computers has been mostly lost from our world today. Computers are so complicated and work so reliably nowadays that many of the finer aspects of computing are now little more than dim memories in the minds of some older hackers, or little-read publications gathering dust in libraries somewhere. People often try to get away with knowing as little as they can, and while they might be able to get away with that, it's distressing how many people who believe themselves to be knowledgeable about computers are actually unaware of some highly fundamental concepts. This tiny tutorial will do wonders to your existing cable and DSL modem.
This tiny tutorial will do wonders to your existing cable and DSL modem. n a nutshell, network topologies are the physical alignments of computers and the way they are connected to each other. For example, if all the computers are connected to each other via a central device (Hub or Switch), the type of topology is Star. Likewise, if all the computers are connected to each other via a main cable, this means it is Bus Topology.
n a nutshell, network topologies are the physical alignments of computers and the way they are connected to each other. For example, if all the computers are connected to each other via a central device (Hub or Switch), the type of topology is Star. Likewise, if all the computers are connected to each other via a main cable, this means it is Bus Topology.
